At VDA Labs we get excited about Reverse Engineering tools, and the release of NSA’s GHIDRA was valuable to the industry. The fact that it is free, supports many different CPU architectures, contains decompiler functionality, and allows many Reverse Engineers to work on the same project via a Team server, are some of the highlights. Another area of immediate interest to us was the scripting functionality. Much like IDA Pro, it is very easy to write scripts to help automate Reverse Engineering tasks.
A Quick Script
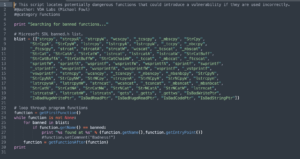
While researching the functionality, VDA Labs wrote a script that searches through a program for the use of any unsafe functions. While not overly complicated, it demonstrates how fast and easy it is to extend GHIDRA’s functionality. We hope you have as much fun scripting GHIDRA as us!
Get the script at VDA Labs’ Github!
How to Run a GHIDRA Script
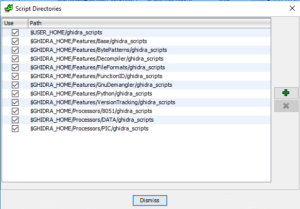
Running one of the 238 included scripts, or adding your script is quite easy. Simply drop the script on one of these directories.
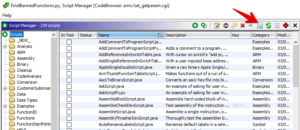
Another option is creating your script in the “Script Manager” interface.
After creating the “FindBannedFunctions.py” GHIDRA script, simply run it on any program like is shown below.
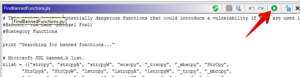
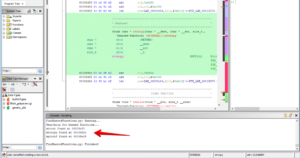
The output for an example ARM program we are reversing in some of our previous IoT hacking blogs, should look something like the screen capture below.
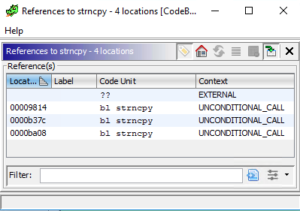
Simply double-click any of the identified memory addresses to visit the Banned Function entry point. Once there, you can press “Ctrl-Shift-F” to find any Cross-references where the Banned Function is used in the application. Happy GHIDRA scripting! And if you need any reverse engineering support — we’d love to help.
-
Previous Post
Creating Mayhem: Crashing MP3gain for Fun and CVEs